Summary
Ransomware attacks have evolved as threat actors continually seek ways to expand the scope of their operations and increase profitability. The ransomware-as-a-service (RaaS) model became popular because the use of affiliates enables ransomware operators to attack more victims with little effort. It also created opportunities for threat actors with limited technical skills to benefit from the ransomware economy. Name-and-shame attacks increased potential for financial gain by combining threats of data disclosure and file encryption to extort victims. Although law enforcement response to a high-profile attack on U.S. critical infrastructure prompted ransomware operators, affiliates, and owners of various underground forums to rethink their strategies, Secureworks® Counter Threat Unit™ (CTU) researchers have observed the threat actors adapting tactics and continuing operations.
A brief history of ransomware
Ransomware emerged in the late 1980s when a medical researcher attempted to extort other researchers via malware delivered on floppy disks. Subsequent ransomware evolution was slow. Deployment did not become common until the mid-2000s, when threat actors extorted payment by denying victims access to their own services and systems.
Campaigns in the mid-2010s relied on indiscriminate distribution to a large number of victims. An automated "fire-and-forget" approach leveraged phishing campaigns and vulnerability scanning to deploy ransomware to a single host or a small number of hosts. While this approach targeted many victims, the attacks were often unsuccessful. The ransomware's propagation lacked control and did not cause sufficient disruption to compromised networks. As a result, victims rarely complied with the extortion demands. Ransom demands were relatively low by today's standards.
In 2015, cybercriminal groups began deploying post-intrusion ransomware. The GOLD LOWELL threat group was the first to use this tactic, deploying the SamSam ransomware to compromised systems. The operators of the Ryuk, BitPaymer, and Defray ransomware families quickly followed suit. The defining characteristic of post-intrusion ransomware attacks is the hands-on-keyboard activity that threat actors use to maximize the malware's destructive capabilities. This shift reduced the number of victims that a single threat group could exploit, but it gave the operators much more control over ransomware deployment, enabled the targeted and successful encryption of files on the network, and justified demands for higher ransoms. These factors encouraged more cybercriminals to get involved in ransomware activity.
The next major development was the ransomware-as-a-service (RaaS) business model. Ransomware operators started to engage affiliates to deploy malware for a share of the ransom payment. This model enabled operators to scale operations and significantly lowered the barrier to entry for this type of crime. Even threat actors with a low level of technical skill have successfully stolen money and destroyed large parts of victims' networks by leveraging RaaS in post-intrusion ransomware incidents.
The introduction of the “name-and-shame” tactic, first observed in April 2019 Snatch ransomware operations, was a significant development. The GOLD VILLAGE threat group began fully exploiting the tactic in late 2019, threatening to publish data stolen during Maze ransomware operations on the group's leak site if victims did not pay the ransom. By March 2020, CTU™ researchers had observed three other groups conducting name-and-shame ransomware activity. Adoption continued to expand as the operations proved profitable. As of June 21, 2021, CTU researchers track 27 ransomware operations using this tactic.
Ransom demands have dramatically increased. During nine months spanning 2013 and 2014, the CryptoLocker operators collected a total of $3 million USD. In 2020, the average ransom that the now-defunct Maze ransomware group demanded from a single victim was reportedly $4.8 million. The GOLD WATERFALL threat group that operates the Darkside ransomware reportedly accumulated $90 million in less than a year of operation. In late March 2021, a U.S. insurance provider allegedly paid $40 million to regain access to its network following the deployment of a Hades ransomware variant operated by the GOLD WINTER threat group.
Government-sponsored threat groups use ransomware to generate revenue or cause damage. For example, likely Iranian threat groups used N3tw0rm and Pay2Key ransomware to disrupt services at Israeli companies in early 2021. The 2017 NotPetya incident, arguably one of the most destructive cyberattacks, masqueraded as ransomware but was subsequently attributed to a Russian military operation to undermine Ukraine's critical national infrastructure. North Korea has long used ransomware to generate revenue, leveraging GandCrab v4 against South Korean targets in 2018 and VHD ransomware against high-profile companies in 2020. WCry (also known as WannaCry), also one of the most disruptive ransomware attacks, was a North Korean cyber operation. While government-sponsored ransomware operations can be disruptive, criminal ransomware attacks pose a far greater threat to most organizations. Therefore, this analysis focuses on the criminal use of ransomware for financial gain.
Name and shame
Many criminal ransomware groups operate name-and-shame schemes (see Table 1). As of June 21, 2021, more than one-third of these operations offer RaaS, another third likely have RaaS offerings, and the remaining are traditional schemes. The operators retain a higher percentage of the profits in traditional operations, but those schemes do not scale as effectively.
| Astro Team | LockBit | Prometheus |
| Avaddon | Lorenz | RagnarLocker |
| Clop (GOLD TAHOE) | LV (GOLD NORTHFIELD) | Ragnarok |
| Conti (GOLD ULRICK) | Pysa (GOLD BURLAP) | 777 (GOLD DUPONT) |
| Cuba | Mount Locker | Ranzy |
| Darkside (GOLD WATERFALL) | Nefilim (GOLD MANSARD) | REvil (GOLD SOUTHFIELD) |
| DoppelPaymer (GOLD HERON) | NoName | SunCrypt |
| Everest | Marketo | SynACK |
| Grief | Payload.bin (formerly Babuk) |
Table 1. Active name-and-shame ransomware operations and associated threat groups (if known) as of June 21, 2021
All name-and-shame ransomware operations require access to a compromised network to steal victims' data and to position and deploy ransomware. In traditional schemes, the operators perform the various functions essential to successful deployment, with the occasional exception of relying on an initial access broker (IAB) to gain initial access to the network. In the RaaS model, some important functions are conducted by the ransomware affiliates (see Figure 1).
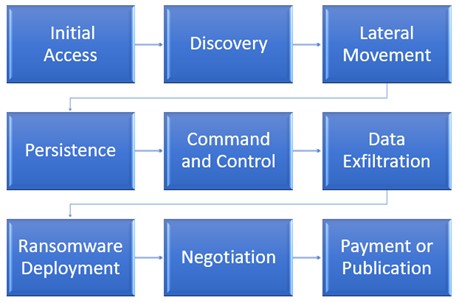
Figure 1. Name-and-shame ransomware process. (Source: Secureworks)
RaaS ecosystem
The RaaS model is widely adopted in name-and-shame ransomware operations. There are three roles in this model: operators, affiliates, and IABs.
Operators
The operators are the threat groups that build and maintain the ransomware. In the RaaS model, the operators outsource processes such as gaining access to victims' networks and deploying the ransomware to affiliates rather than performing these actions themselves. The operators typically conduct the payment negotiations with victims in both the traditional and RaaS models. These criminal threat groups generally do not have political motivation. However, many ransomware operators are based in Russia and Commonwealth of Independent States (CIS) countries, where they enjoy a relative freedom to operate so long as they refrain from targeting Russian companies or organizations. Their campaigns may inadvertently and indirectly support the objectives of the Russian government, as disruption of certain Western corporations' business operations aligns with the Russian government's political and economic objectives.
Ransomware groups operate independently of each other and do not appear to coordinate their activity. However, some affiliates may work with more than one operator. Furthermore, affiliates may mature into ransomware operators.
- The GOLD SOUTHFIELD threat group that created the REvil RaaS was originally an affiliate of the GandCrab RaaS, whose operators announced their 'retirement' at the end of May 2019. In October, the GOLD SOUTHFIELD threat actors claimed that they purchased the GandCrab source code.
- GOLD WATERFALL was a REvil affiliate before developing and deploying Darkside. At the end of May 2021, information about a victim allegedly targeted by Darkside appeared on the REvil leak site.
- The BitPaymer ransomware operated by the GOLD DRAKE threat group was subsequently reworked and renamed DoppelPaymer by the GOLD HERON threat group. GOLD HERON threat actors were former members of GOLD DRAKE.
Affiliates
Affiliates access victims' networks and deploy ransomware. These affiliates are individuals or small teams that partner with the RaaS operators. This business arrangement greatly increases the number of organizations that can be targeted concurrently, but attack sophistication can vary when affiliates have different skill levels.
Affiliates are often referred to as 'networkers' on underground forums, as they gain access to and then 'work' a victim's network. An affiliate obtains access to one or more compromised networks by conducting phishing attacks, exploiting vulnerabilities, leveraging a malware distribution service that sells access to systems that have been compromised with downloader malware, or buying credential-based access from an IAB on an underground forum.
The success of a RaaS operation requires that ransomware groups attract the best affiliates. Some threat groups have advertised their services, using various factors to compete with rivals. Whether privately or publicly, operators may highlight their ransomware's capabilities (e.g., encryption speed and payment facilities), list the platforms the software supports (e.g., Windows, Linux, ESXi, Hyper-V), and stipulate their desired types of network access (e.g., VPN, RDP). RaaS operators could specify additional functions like distributed denial of service (DDoS) to entice affiliates from other services or cite global media articles to prove legitimacy. The number of affiliates an operator is able to work with at any one time (known as the number of “seats”), the percentage of profits, affiliate support options, mechanisms used to negotiate with and pressure victims, and payment processes can also attract candidates.
- By building robust ransomware with broad platform compatibility, operators can broaden the scope of potential victims and ensure maximum profitability. In underground forum advertisements observed by CTU researchers, Avaddon operators claimed their ransomware was compatible with older systems such as Windows XP and Windows 2003, while the Darkside and Babuk operators claimed that their ransomware could be deployed against VMWare ESXi and Synology NAS. Babuk could also allegedly target Hyper-V and QNAP.
- The number of affiliate seats varies; for example, Babuk operators claimed they could support two affiliates concurrently, while REvil can support 10. The profit share each operator offers also varies and can change depending on the affiliate's experience, the type of access they provide, and the ransom amount paid by the victim. The percentages range from 25-40% offered for Avaddon operations to 75-90% for Darkside. RaaS operators adapt to circumstances to ensure continued operation in a competitive marketplace. In February 2021, the Avaddon operators announced a temporary increase in profit share to 80% after a third party released a decryptor for the ransomware that would have undermined its profitability (see Figure 2).

Figure 2. Avaddon operators' response to the release of a decryptor. (Source: Secureworks)
- Operators offer different types of support to compete for the best affiliates. For example, Avaddon operators advertised 24/7 support via a chat and ticket system.
- The negotiation process with victims differs across groups. The Darkside RaaS implemented a communication module that automatically scheduled telephone calls. Tactics such as DDoS have been used in Avaddon and REvil operations to increase pressure on the victim. GOLD TAHOE, which operates the Clop ransomware, extorted additional ransoms by sending email messages to the victim's customers, encouraging them to prevent the release of sensitive data that the threat actors exfiltrated from the victim's network (see Figure 3).

Figure 3. Clop email to victim's customers. (Source: Secureworks)
- Ransom payments are always required in cryptocurrency. Most groups require Bitcoin, although GOLD SOUTHFIELD and GOLD WATERFALL have accepted Monero in the past. Some groups have automated the payment process to affiliates. For example, GOLD WATERFALL pays affiliates with mixed (also known as 'tumbled') cryptocurrencies to obfuscate the transit of cash between wallets and limit the chances of detection and seizure.
While ransomware operators can exaggerate their capabilities, false statements have been exposed in reviews by disappointed affiliates (see Figure 4). Unfavorable reviews can damage the RaaS brand and reduce its profitability.

Figure 4. User review of Avaddon RaaS on underground forum and operator response. (Source: Secureworks)
Affiliates contact operators, sometimes in response to recruitment advertisements, and provide their qualifications for consideration (see Figure 5).

Figure 5. Affiliate applicant responding to REvil advertisement on underground forum. (Source: Secureworks)
The RaaS operators interview applicants and sometimes require proof of revenue from previous ransomware engagements. After an affiliate is accepted, they are issued a unique identifier and receive the ransomware executable. Affiliates must be skilled at gaining and maintaining access. They must also be able to identify backup servers and file servers to achieve maximum effect. Most operators refuse to work with affiliates who only speak English (see Figure 6).

Figure 6. REvil operator response on underground forum indicating the group does not work with English speakers. (Source: Secureworks)
An affiliate's lack of experience can limit which ransomware groups accept them. For example, an affiliate with no or few successes may be forced to work with a lesser known or newer RaaS offering. Well-established RaaS operators can be selective. For example, applicants to the Babuk RaaS operation were required to deposit $15,000 USD on the 'exploit . in' forum before they would be considered for inclusion. This requirement was likely to discourage law enforcement personnel, researchers, inexperienced threat actors, and individuals without serious intent.
Each RaaS operation has a limited number of seats, so affiliates may move to another RaaS operation once a campaign is complete. It is likely that affiliates and RaaS operators form enduring relationships when mutually beneficial.
Initial access brokers
Ransomware operators and affiliates can also buy access from IABs. Access brokering on underground forums is widespread. IABs likely use publicly available scanning tools to identify vulnerabilities and indiscriminately exploit those flaws. IABs may not have advanced technical skills; they could use established techniques to exploit long-standing vulnerabilities in common software and systems. IABs then sell the access to the highest bidder.
Although network access sold by IABs may not be advertised for ransomware operations, it could be repurposed for ransomware deployment if it meets the operators' requirements. In those cases, the operators or affiliates pay the IAB a one-time advertised or negotiated fee, likely based on the type of access. For example, access to domain administrator accounts or domain controllers commands a higher premium. It is unclear how relationships between IABs and the operator or affiliate evolve. As with any business relationship, ongoing associations likely form when they are profitable for both parties.
Victimization
CTU analysis indicates that most ransomware attacks are opportunistic rather than targeted. Operators may choose to infect systems based on available access, the perceived maturity of a potential victim's security controls, and the victim's annual revenue. Some ransomware groups may prioritize certain victims due to perceived success. For example, attacks on manufacturing organizations demonstrated that forcing critical manufacturing processes offline provides a strong incentive for the victim to pay the ransom. Victim selection is not the same as targeting. Ultimately, attacks occur where access can be most easily obtained and maintained.
RaaS operators provide affiliates with incentives for victims that exceed a predetermined revenue base. Some operators stipulate industry verticals that their affiliates must avoid (e.g., healthcare, education, non-profit organizations, critical infrastructure). Conversely, GOLD ULRICK operators appear to impose no restrictions on their operations, with affiliates showing no compunction for targeting healthcare organizations with Conti ransomware. None of the RaaS operators tracked by CTU researchers allow targeting of organizations in the Commonwealth of Independent States (CIS).
In March 2021, GOLD SOUTHFIELD member 'Unknown' indicated that REvil operators will select future victims by targeting cyber insurance providers and identifying their customers. This is presumably because organizations with cyber insurance are more likely to pay a ransom. After exhausting the client list, the threat group allegedly extorts the insurance company. CTU researchers have no evidence to verify these claims, but insurance companies have appeared on leak sites. However, it is unclear how the stolen data was used to identify additional victims. 'Unknown' also suggested that GOLD SOUTHFIELD notifies ransomware negotiation companies of new victims, possibly to encourage negotiators to introduce themselves to victims.
The number of victims differs across ransomware families. These differences likely depend on the ease of deployment, the ransomware's effectiveness, and the overall size of the RaaS operation. Limiting factors include hardware, development resources, and developer availability. Table 2 lists statistics for name-and-shame groups as of June 21, 2021 based on monitored leak site activity.
| Ransomware | Date first victim was posted | Totals days of operation | Number of published victims | Average number of victims posted per 30 days |
|---|---|---|---|---|
| Conti | 2019-11-29 | 570 | 417 | 22 |
| Maze | 2019-12-07 | 334 | 266 | 24 |
| REvil | 2019-05-01 | 782 | 259 | 10 |
| Egregor | 2020-09-18 | 103 | 206 | 60 |
| DoppelPaymer | 2019-07-02 | 720 | 200 | 8 |
| Pysa | 2019-10-11 | 619 | 189 | 9 |
| Avaddon | 2020-06-01 | 373 | 182 | 15 |
| NetWalker | 2019-09-05 | 509 | 144 | 8 |
| Darkside | 2020-08-01 | 285 | 99 | 10 |
| Clop | 2019-02-01 | 871 | 65 | 2 |
| Babuk | 2021-01-04 | 168 | 43 | 8 |
| LV | 2021-04-09 | 73 | 40 | 16 |
| Netfilm | 202-03-14 | 464 | 40 | 3 |
| Everest | 2020-12-01 | 202 | 39 | 6 |
| Prometheus | 2021-03-28 | 85 | 37 | 13 |
| Ragnarok | 2020-01-01 | 537 | 33 | 2 |
| Marketo | 2021-04-13 | 69 | 32 | 14 |
| RagnarLocker | 2020-02-04 | 503 | 27 | 2 |
| Suncrypt | 2020-08-25 | 300 | 22 | 2 |
| RansomExx | 2020-06-17 | 369 | 21 | 2 |
| Mount Locker | 2020-07-01 | 355 | 20 | 2 |
| 2021-04-29 | 53 | 18 | 10 | |
| Lorenz | 2021-04-29 | 53 | 17 | 10 |
| Astro Team | 2021-03-02 | 111 | 16 | 4 |
| Grief | 2021-05-27 | 25 | 15 | Not applicable |
| AKO | 2020-01-09 | 181 | 9 | 1 |
| Cuba | 2020-12-01 | 202 | 9 | 1 |
| LockBit | 2019-10-19 | 611 | 9 | 0 |
| Sekhmet | 2020-03-18 | 103 | 6 | 2 |
| Snatch | 2019-05-01 | 16 | 6 | Not applicable |
| NoName | 2021-04-28 | 54 | 6 | 3 |
| SynACK | 2021-03-28 | 85 | 6 | 2 |
| Ranzy | 2020-08-18 | 307 | 3 | 0 |
| Payload bin | 2021-05-31 | 21 | 2 | Not applicable |
| Nemty | 2020-03-03 | 1 | 1 | Not applicable |
Table 2. Ransomware leak site statistics as of June 21, 2021, listed in descending order of number of published victims. Italics indicate likely inactive operations.
Older and well-established ransomware groups have compromised the most victims, but the frequency (number of victims per month) is evenly distributed across a long time span. This table likely does not depict the full range of victims; it may not include victims that paid the ransom within the specified timeframe and were not listed on the leak site. For example, when Avaddon operators shuttered their operation, they released decryption keys for 2,934 victims. This figure is substantially higher than the 373 victims they named on their leak site. Ransomware groups could also post false information. For example, a group could remove a victim's name from the leak site despite lack of payment to appear more effective and attractive to potential affiliates. The removal could also suggest to potential victims that the group can be trusted to remove a victim's data after receiving the ransom payment.
Further developments
Some name-and-shame groups may have shifted from ransomware deployment to focus on data theft. Victims that were compromised via the Accellion FTA vulnerability in December 2020 and January 2021 were listed on the Clop leak site, but the threat actors just stole data without deploying the Clop ransomware. Babuk operators converted to a RaaS approach in January 2021 and then announced at the end of April that they were focusing exclusively on data theft for extortion. Victims were posted to the Babuk leak site after the announcement, but the nature of these intrusions is unknown. It appears that the Babuk operators launched the Payload . bin leak site after they stopped listing victims on the Babuk leak site in mid-May. The group announced that it was using Payload . bin to host leak data from ransomware groups that did not have dedicated platforms.
The Colonial Pipeline attack on May 7 led to changes in RaaS offerings and marketing. The attack caused significant disruption to the delivery of fuel to consumers in eastern U.S. states, and the U.S. Federal Bureau of Investigation (FBI) attributes it to GOLD WATERFALL. GOLD WATERFALL (Darkside) responded by ending its RaaS operations on May 13, and it is unclear how this group will operate in the future. GOLD SOUTHFIELD (REvil) also announced it was ceasing its RaaS operation but did not indicate that it was refraining from deploying ransomware. As of June 21, the group continues to post victims to its leak site. On June 11, the Avaddon operators shuttered their operation. The underground forums on which RaaS operators and affiliates advertise their services (e.g., exploit . in, RaidForums, XSS) announced prohibitions on ransomware-related posts. Despite these changes, name-and-shame operations have continued. Between May 13 and June 21, two ransomware groups emerged and 269 victims' names were posted across 19 leak sites. CTU researchers have observed threat actors using vague or “coded” language to circumvent underground forums' ban on ransomware discussions (see Figures 7 and 8).

Figure 7. Underground forum advertisement likely by a potential affiliate, carefully worded to circumvent ransomware ban. (Source: Secureworks)

Figure 8. Underground forum advertisement likely by a ransomware operator, carefully worded to circumvent ransomware ban. (Source: Secureworks)
Conclusion
Name-and-shame ransomware will continue as long as it remains profitable for cybercriminal groups. Competition in the market drives the evolution of ransomware capabilities, the distribution methods used to deploy it, and the incentives offered by RaaS operators to attract skilled affiliates. Law enforcement intervention could force some ransomware groups to adapt. While some ransomware families may disappear, the threat groups could reemerge with new ransomware or different tactics. By avoiding organizations that significantly impact critical infrastructure or public services, most RaaS operations could likely operate below the threshold at which public opinion will force a more aggressive law enforcement response.
Organizations should apply layered security controls and test those controls against a ransomware attack scenario. Relying solely on offline backups as a failsafe could be inadequate if the organization possesses data that must not be published on the internet. CTU researchers recommend that organizations review the tactics, techniques, and procedures (TTPs) used by known ransomware groups. Organizations should implement preventive controls that reduce the organization's attack surface and frustrate opportunistic affiliates and IABs, and controls that enable quick detection and response during an intrusion. Detecting activity in the initial phases of an attack (e.g., internal reconnaissance, lateral movement) will become increasingly critical if threat groups more widely adopt name-and-shame operations that eliminate ransomware. The shorter process gives network defenders less time to mitigate the impact.
References
Abrams, Lawrence. “Avaddon ransomware shuts down and releases decryption keys.” Bleeping Computer. June 11, 2021. https://www.bleepingcomputer.com/news/security/avaddon-ransomware-shuts-down-and-releases-decryption-keys/
Accellion. “Mandiant Identifies Criminal Threat Actor and Mode of Attacks.” February 22, 2021. https://www.accellion.com/company/press-releases/accellion-provides-update-to-fta-security-incident-following-mandiants-preliminary-findings/
Alvarado, Alec. “Not Another Ransomware Blog: Initial Access Brokers And Their Role.” Digital Shadows. September 9, 2020. https://www.digitalshadows.com/blog-and-research/not-another-ransomware-blog-initial-access-brokers-and-their-role/
Castillo, Donald. “.EGG Files in Spam Delivers GandCrab v4.3 Ransomware to South Korean Users.” Trend Micro. August 20, 2018. https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/-egg-files-in-spam-delivers-gandcrab-v4-3-ransomware-to-south-korean-users
DISSENT. “A former DarkSide listing shows up on REvil's leak site.” DataBreaches.net. May 26, 2021. https://www.databreaches.net/a-former-darkside-listing-shows-up-on-revils-leak-site/
DISSENT. “Babuk re-organizes as Payload Bin, offers its first leak.” DataBreaches.net. May 31, 2021. https://www.databreaches.net/babuk-re-organizes-as-payload-bin-offers-its-first-leak/
Fox-IT. “CryptoLocker ransomware intelligence report.” August 6, 2014. https://blog.fox-it.com/2014/08/06/cryptolocker-ransomware-intelligence-report/
Heller, Michael. “Maze gang outs ransomware victims in shame campaign.” TechTarget. December 17, 2019. https://searchsecurity.techtarget.com/news/252475664/Maze-gang-outs-ransomware-victims-in-shame-campaign
KnowBe4. “AIDS Trojan or PC Cyborg Ransomware.” Accessed June 7, 2021. https://www.knowbe4.com/aids-trojan
Kwiatkowski, Ivan. “Lazarus on the hunt for big game.” Securelist by Kaspersky. July 28, 2020. https://securelist.com/lazarus-on-the-hunt-for-big-game/97757/
Mehrotra, Kartikay and Turton, William. “CNA Financial Paid $40 Million in Ransom After March Cyberattack.” Bloomberg. May 20, 2021. https://www.bloomberg.com/news/articles/2021-05-20/cna-financial-paid-40-million-in-ransom-after-march-cyberattack
Robinson, Tom. “DarkSide Ransomware has Netted Over $90 million in Bitcoin.” Elliptic. May 18, 2021. https://www.elliptic.co/blog/darkside-ransomware-has-netted-over-90-million-in-bitcoin
Secureworks. “Hades Ransomware Operators Use Distinctive Tactics and Infrastructure.” June 15, 2021. https://www.secureworks.com/blog/hades-ransomware-operators-use-distinctive-tactics-and-infrastructure
Secureworks. “LV Ransomware.” June 22, 2021. https://www.secureworks.com/research/lv-ransomware
Secureworks. “Preparing for Post-Intrusion Ransomware.” June 29, 2020. https://www.secureworks.com/blog/preparing-for-post-intrusion-ransomware
Secureworks. “REvil/Sodinokibi Ransomware.” September 24, 2019. https://www.secureworks.com/research/revil-sodinokibi-ransomware
Secureworks. “REvil: The GandCrab Connection.” September 24, 2019. https://www.secureworks.com/blog/revil-the-gandcrab-connection
Secureworks. “SamSam Ransomware Campaigns.” February 15, 2018. https://www.secureworks.com/research/samsam-ransomware-campaigns
Secureworks. “WCry Ransomware Analysis.” May 19, 2017. https://www.secureworks.com/research/wcry-ransomware-analysis
Smilyanets, Dmitry. “'I scrounged through the trash heaps...now I'm a millionaire:' An interview with REvil's Unknown.” The Record by Recorded Future. March 16, 2021. https://therecord.media/i-scrounged-through-the-trash-heaps-now-im-a-millionaire-an-interview-with-revils-unknown/
Sophos. “The State of Ransomware 2021.” April 2021. https://secure2.sophos.com/en-us/medialibrary/pdfs/whitepaper/sophos-state-of-ransomware-2021-wp.pdf
Stracqualursi, Veronica; Sands, Geneva; and Saenz, Arlette. “Cyberattack forces major US fuel pipeline to shut down.” CNN. May 8, 2021. https://edition.cnn.com/2021/05/08/politics/colonial-pipeline-cybersecurity-attack/index.html
UK National Cyber Security Centre. “Russian military 'almost certainly' responsible for destructive 2017 cyber attack.” February 14, 2018. https://www.ncsc.gov.uk/news/russian-military-almost-certainly-responsible-destructive-2017-cyber-attack
Unit 42. “Highlights from the 2021 Unit 42 Ransomware Threat Report.” Palo Alto Networks. March 17, 2021. https://unit42.paloaltonetworks.com/ransomware-threat-report-highlights/
U.S. Federal Bureau of Investigation. “FBI Statement on Compromise of Colonial Pipeline Networks.” May 10, 2021. https://www.fbi.gov/news/pressrel/press-releases/fbi-statement-on-compromise-of-colonial-pipeline-networks